Raxis Blog Posts by Category
-
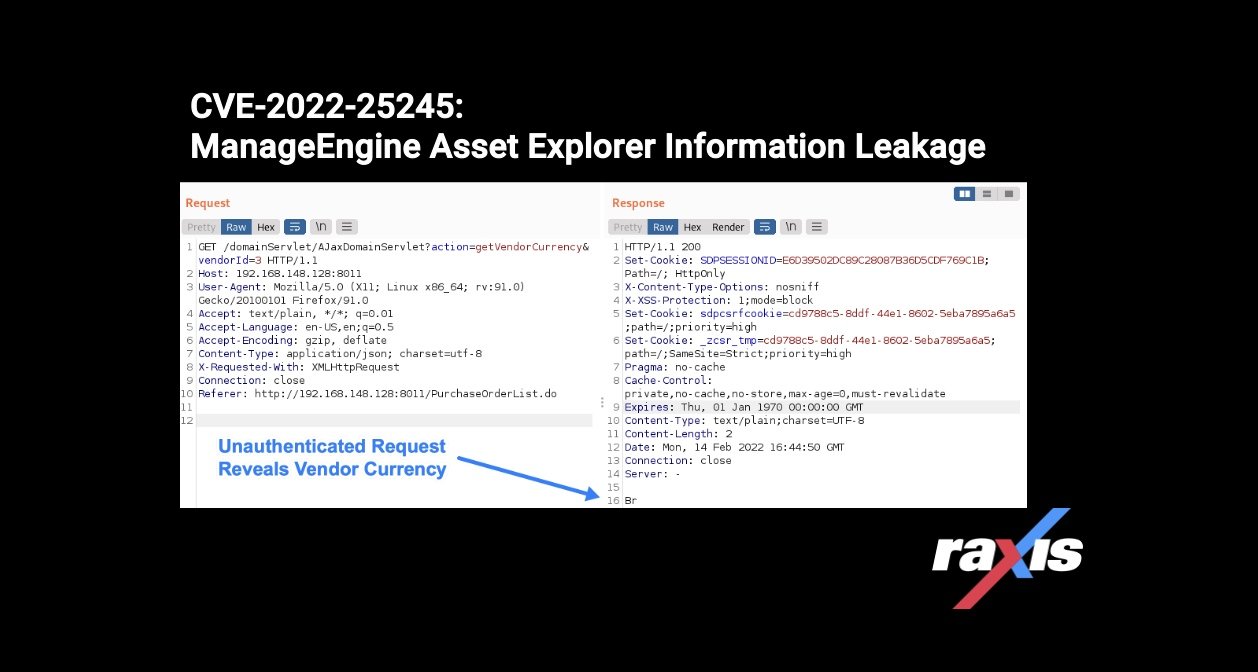 CVE-2022-25245: ManageEngine Asset Explorer Information LeakageRaxis lead penetration tester Matt Dunn discovers an information leakage vulnerability in ManageEngine’s Asset Explorer CVE-2022-25245
CVE-2022-25245: ManageEngine Asset Explorer Information LeakageRaxis lead penetration tester Matt Dunn discovers an information leakage vulnerability in ManageEngine’s Asset Explorer CVE-2022-25245 -
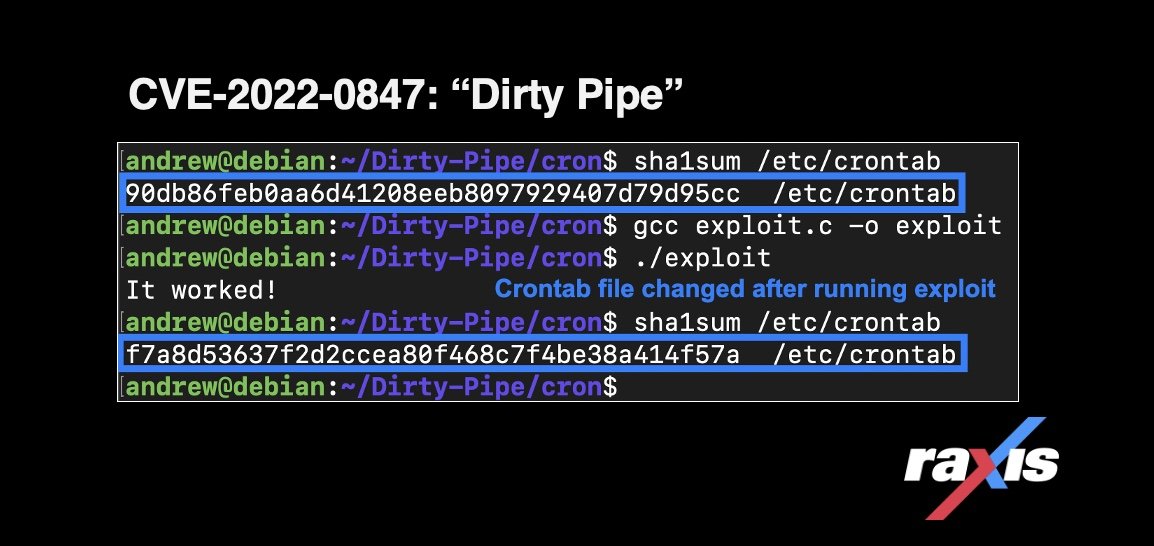 Exploiting Dirty Pipe (CVE-2022-0847)The Dirty Pipe vulnerability (CVE-2022-0847) allows any user to write to read-only files, including files that are owned by root, allowing privilege escalation.
Exploiting Dirty Pipe (CVE-2022-0847)The Dirty Pipe vulnerability (CVE-2022-0847) allows any user to write to read-only files, including files that are owned by root, allowing privilege escalation. -
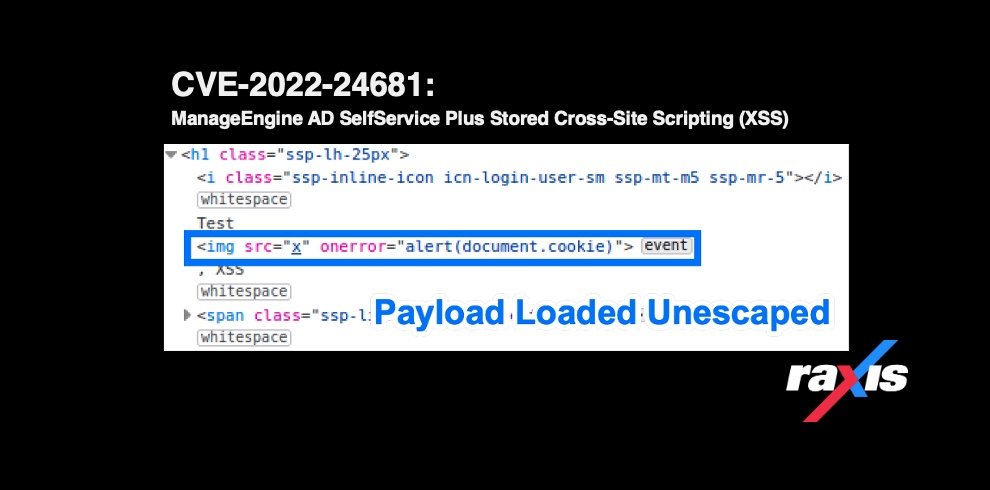 CVE-2022-24681: ManageEngine AD SelfService Plus Stored Cross-Site Scripting (XSS)Raxis lead penetration tester Matt Dunn continues his prolific discovery of new cross-site scripting CVEs. This one affects ManageEngine AD SelfService Plus Stored Cross-Site Scripting (XSS).
CVE-2022-24681: ManageEngine AD SelfService Plus Stored Cross-Site Scripting (XSS)Raxis lead penetration tester Matt Dunn continues his prolific discovery of new cross-site scripting CVEs. This one affects ManageEngine AD SelfService Plus Stored Cross-Site Scripting (XSS). -
 Hackers See Opportunity Where You See Only a ButtonIn this post, Raxis VP Brad Herring explains how web proxy tools can turn even simple buttons and check-boxes into avenues for an attack.
Hackers See Opportunity Where You See Only a ButtonIn this post, Raxis VP Brad Herring explains how web proxy tools can turn even simple buttons and check-boxes into avenues for an attack. -
 Cross-Site Scripting (XSS): Filter Evasion and SideloadingIn this second in a series, learn how to perform Cross-Site Scripting (XSS) attacks such as filter evasion and sideloading content.
Cross-Site Scripting (XSS): Filter Evasion and SideloadingIn this second in a series, learn how to perform Cross-Site Scripting (XSS) attacks such as filter evasion and sideloading content. -
 OWASP Top 10: Broken Access ControlIn this blog post, Raxis lead penetration tester Mark Fabian discusses broken access control and why it’s the most prevalent issue among the OWASP Top 10.
OWASP Top 10: Broken Access ControlIn this blog post, Raxis lead penetration tester Mark Fabian discusses broken access control and why it’s the most prevalent issue among the OWASP Top 10. -
 2021 OWASP Top 10 Focus: Injection Attacks for Penetration TestingThe latest draft of the OWASP Top 10 has been released. Though injection is #3, Raxis’ Matt Dun explains why that doesn’t mean the threat is any less severe.
2021 OWASP Top 10 Focus: Injection Attacks for Penetration TestingThe latest draft of the OWASP Top 10 has been released. Though injection is #3, Raxis’ Matt Dun explains why that doesn’t mean the threat is any less severe. -
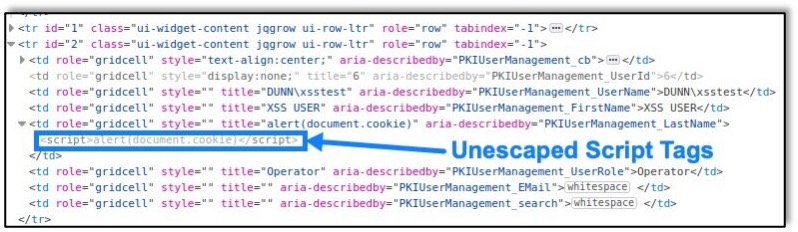 ManageEngine Key Manager Plus Cross-Site Scripting Vulnerability (CVE-2021-28382)Raxis’ Lead Penetration Tester Matt Dunn discovers another cross-site scripting vulnerability in Zoho’s MangeEngine Key Manager Plus (CVE-2021-28382).
ManageEngine Key Manager Plus Cross-Site Scripting Vulnerability (CVE-2021-28382)Raxis’ Lead Penetration Tester Matt Dunn discovers another cross-site scripting vulnerability in Zoho’s MangeEngine Key Manager Plus (CVE-2021-28382). -
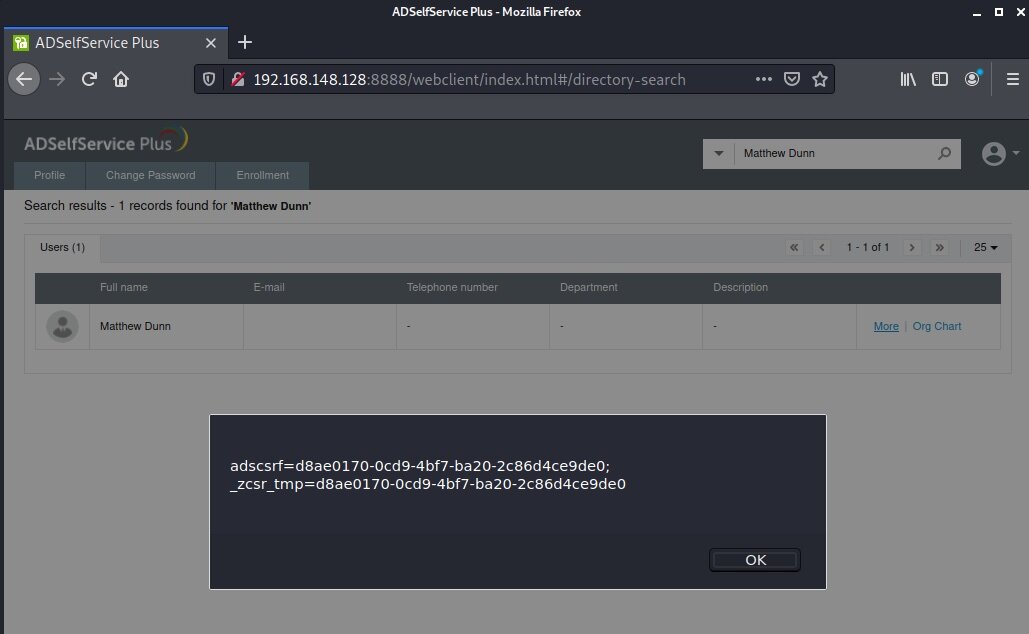 Cross-Site Scripting Vulnerability in ManageEngine AD Self Service Plus (CVE-2021-27956)Raxis lead penetration tester Matt Dunn has uncovered a new cross-site scripting vulnerability in Manage Engine AD Self Service Plus (CVE-2021-27956). Find out more here.
Cross-Site Scripting Vulnerability in ManageEngine AD Self Service Plus (CVE-2021-27956)Raxis lead penetration tester Matt Dunn has uncovered a new cross-site scripting vulnerability in Manage Engine AD Self Service Plus (CVE-2021-27956). Find out more here. -
 LDAP Passback and Why We Harp on PasswordsLDAP passback exploits are easy when companies fail to change default passwords on network devices or fail to assign a password at all. If you connect it, you must protect it.
LDAP Passback and Why We Harp on PasswordsLDAP passback exploits are easy when companies fail to change default passwords on network devices or fail to assign a password at all. If you connect it, you must protect it. -
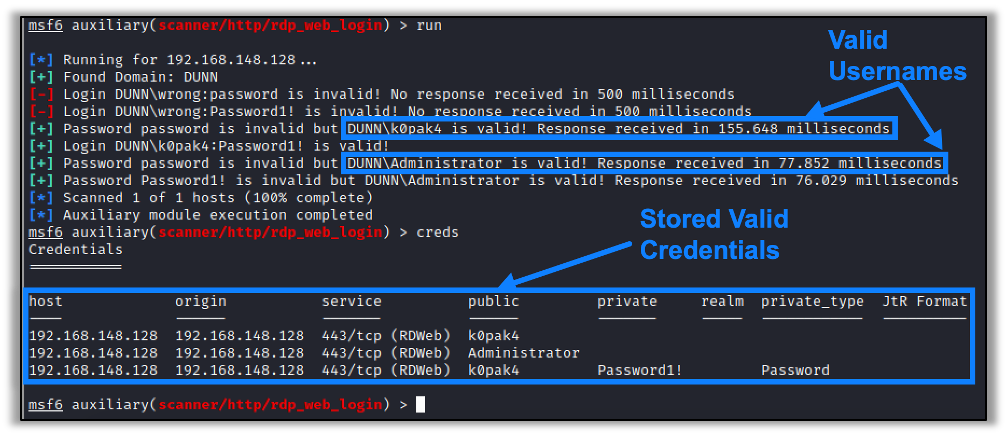 New Metasploit Module: Microsoft Remote Desktop Web Access Authentication Timing AttackRaxis team member Matt Dunn has uncovered a vulnerability in Microsoft’s Remote Desktop Web Access application (RD Web Access). Learn more in this blog article.
New Metasploit Module: Microsoft Remote Desktop Web Access Authentication Timing AttackRaxis team member Matt Dunn has uncovered a vulnerability in Microsoft’s Remote Desktop Web Access application (RD Web Access). Learn more in this blog article. -
 How to Pull Off a Mousejacking AttackRaxis demonstrates how to conduct a mousejacking attack as part of a penetration test.
How to Pull Off a Mousejacking AttackRaxis demonstrates how to conduct a mousejacking attack as part of a penetration test.
Categories
- Careers
- Exploits
- How To
- In The News
- Injection Attacks
- Just For Fun
- Meet The Team
- Mobile Apps
- Networks
- Password Cracking
- Penetration Testing
- Phishing
- PTaaS
- Raxis In The Community
- Red Team
- Security Recommendations
- Social Engineering
- Tips For Everyone
- Unsupported Software Unpatched Systems
- Web Apps
- What People Are Saying
- Wireless
