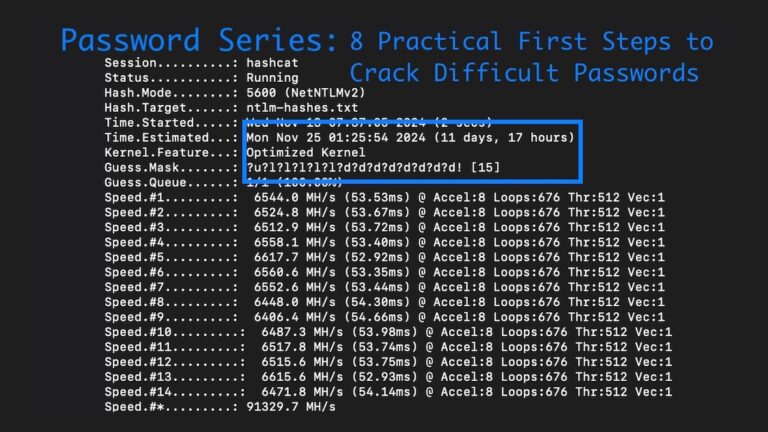
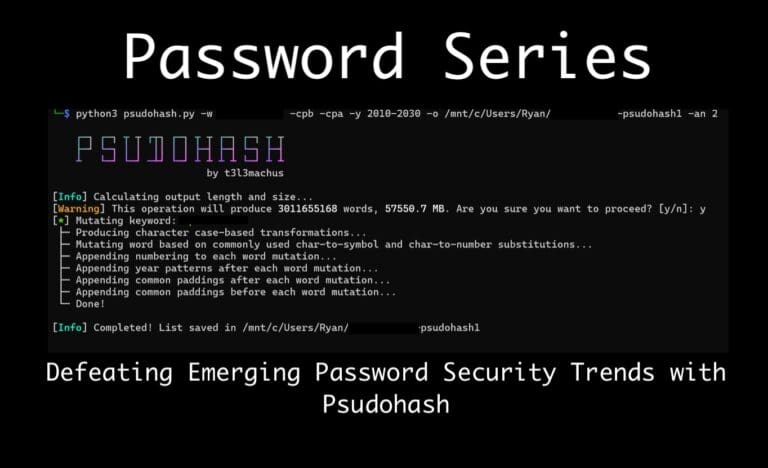
Password Series: 8 Practical First Steps to Crack Difficult Passwords in Penetration Tests
From rulesets & hardware to wordlists and mask attacks, Lead Penetration Tester Ryan Chaplin shows how to crack difficult password hashes in penetration tests.