Lessons from the DaVita Healthcare Ransomware Attack
The DaVita ransomware attack is one of the most impactful recent healthcare breaches. Learn what happened and what could have been done to limit the impact.

The DaVita ransomware attack is one of the most impactful recent healthcare breaches. Learn what happened and what could have been done to limit the impact.

Caroline Kelly concludes our three-part “Choosing a Penetration Testing Company” series with how Penetration Testing as a Service (PTaaS) provides great value.

Brad Herring continues our three-part “Choosing a Penetration Testing Company” series with a look at the factors to consider when choosing the best vendor.

Lead Penetration Tester Jason Taylor takes us step-by-step through jailbreaking an iPad 7 for use in penetration testing.

Cole Stafford starts our three-part “Choosing a Penetration Testing Company” series by looking at what penetration testing is and the types of penetration tests.

What does Penetration Testing as a Service (PTaaS) really mean? In this blog we discuss the details and how do you find the best PTaaS for your organization.

Scoping your penetration test (especially your first one) can be daunting. Our team is always happy to help, and Brad Herring gives you a head start here.
Principal Penetration Tester, Andrew Trexler, dives into Vim, a powerful command line tool for text files, and shows useful commands for penetration testing.

Contrary to common misconceptions, cybersecurity acts as a powerful enabler in the digital age, fostering innovation, driving business growth, and empowering organizations to harness technology’s full potential. By building trust, accelerating innovation, enabling emerging technologies, enhancing efficiency, ensuring compliance, supporting remote work, and protecting intellectual property, robust cybersecurity measures create a secure foundation for organizations to thrive and innovate in an increasingly interconnected world.
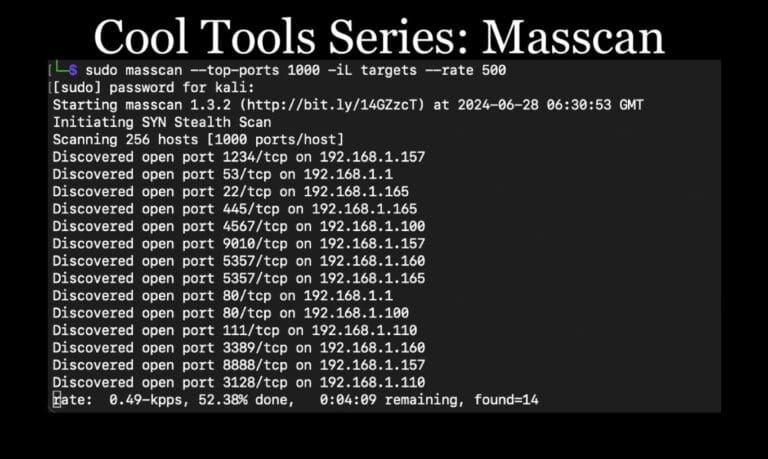
Continuing our Cool Tools Series, Lead Penetration Tester Andrew Trexler shows how to use masscan for discovery scanning on large networks in penetration tests.