Jailbreak Journey: Transforming an iPad for Mobile App Penetration Testing
Lead Penetration Tester Jason Taylor takes us step-by-step through jailbreaking an iPad 7 for use in penetration testing.

Lead Penetration Tester Jason Taylor takes us step-by-step through jailbreaking an iPad 7 for use in penetration testing.

Critical Alert – Patch Immediately. Cisco Releases Patch for CVE-2025-20188 – 10.0 CVSS. This vulnerability affects Cisco Catalyst 9800 wireless controllers.
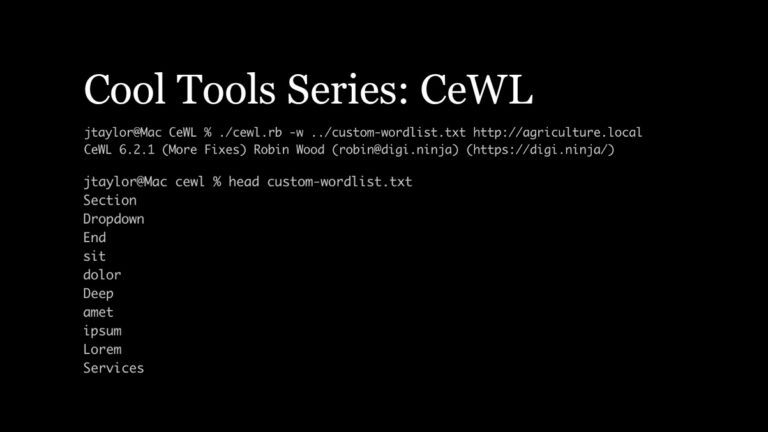
Lead Penetration Tester Jason Taylor discusses how the CeWL Custom Word List generator can improve hashcat results for penetration testing.
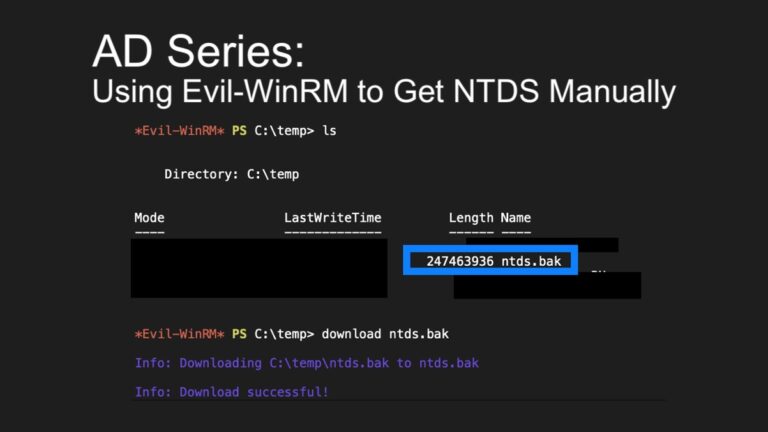
Principal Penetration Tester Andrew Trexler’s Active Directory series is back, showing how to use Evil-WinRM to copy NTDS.dit manually in penetration tests.
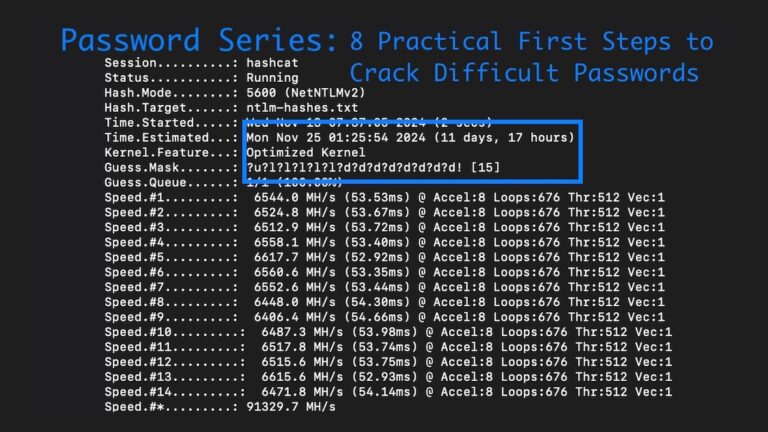
From rulesets & hardware to wordlists and mask attacks, Lead Penetration Tester Ryan Chaplin shows how to crack difficult password hashes in penetration tests.