Wireless Series: The Aircrack-ng Suite for All Your Wireless Pentesting Needs
Principal Penetration Tester Scottie Cole continues our wireless series with the Aircrack-ng Suite, a set of tools for wireless pentest discovery and exploits.
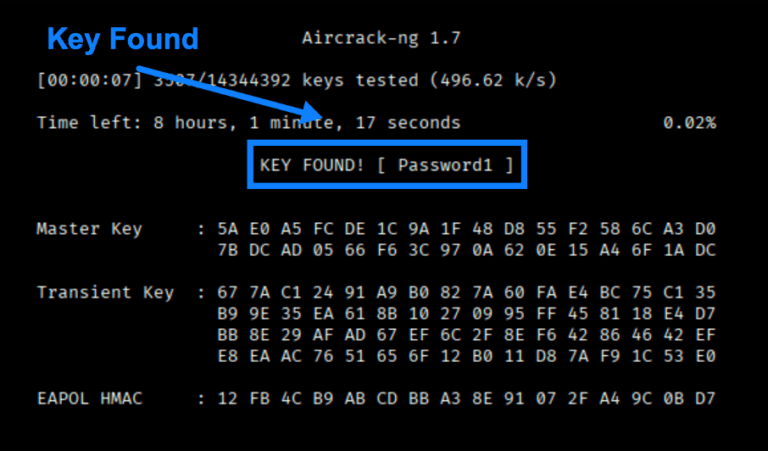
Principal Penetration Tester Scottie Cole continues our wireless series with the Aircrack-ng Suite, a set of tools for wireless pentest discovery and exploits.

Andrew Trexler looks at a recently discovered public database of stolen usernames and passwords and what you can do now to protect your access and information.

With the start of 2026, the Raxis team is already busy. A new upgrade to our password-cracking system shows how quickly 8-character passwords can be cracked.
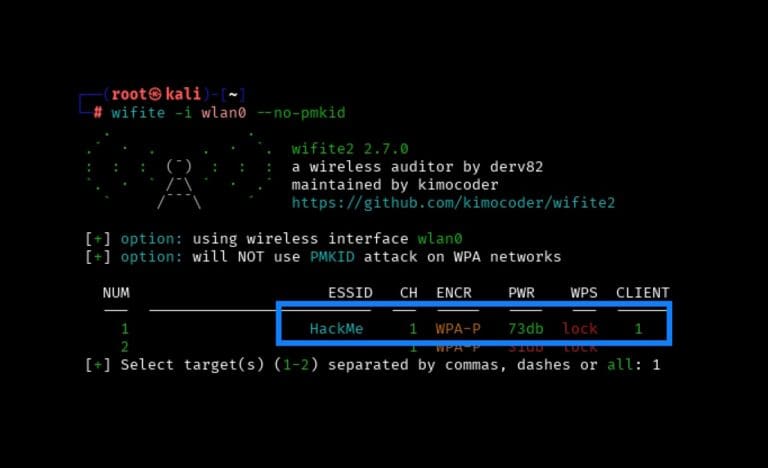
Principal Penetration Tester Scottie Cole begins our wireless penetration testing series with capturing and cracking a WPA2 Pre-Shared Key using Wifite.
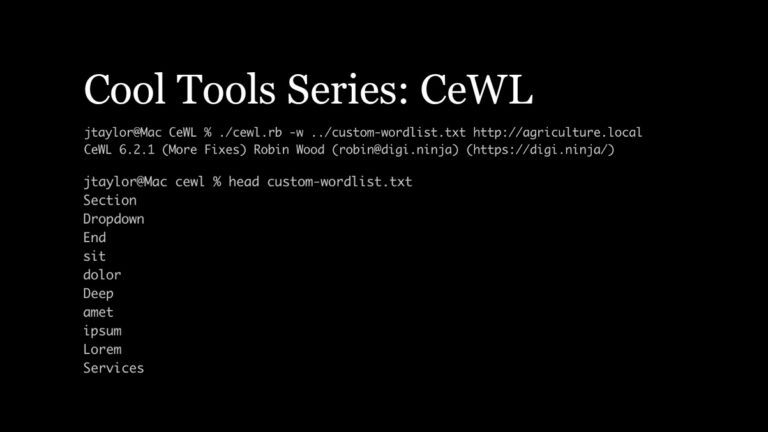
Lead Penetration Tester Jason Taylor discusses how the CeWL Custom Word List generator can improve hashcat results for penetration testing.