Don’t Take the Smishbait
Unwanted text messages are always annoying, but some can be dangerous. Smishing is a phishing attempt carried out via text and it can be more effective than you might think.
We’ve all been there — waiting on an important text message, receiving a notification, and opening the phone only to see a message about our car’s warranty expiring.
Isn’t that just the worst?
As it turns out, no. Far more damaging are the ones that bring phishing and spear-phishing into the more personal, less-guarded world of SMS texting. You’ve probably heard the portmanteau “smishing” (SMS + phishing) to describe the practice, but you may wonder how and why it works. More importantly, you should know what you can do to make sure it doesn’t happen to you.
The psychology of smishing
At its essence, smishing is a form of social engineering that relies on the implied urgency and intimacy of a text message. Whereas most businesses have effective spam and virus filters in place, and we’re reminded often about the dangers of email, text messages often bypass company security. What’s more, they occupy a different place in our minds than standard business communications.
If email reflects the type of discussion you might have in the conference room, texting is more like banter over drinks after work. In the former, we’re conscious about what we say and what we hear. In the latter, we’re more relaxed and trusting of those around us. And, like other forms of social engineering, that’s what hackers count on when they send a smish.
Enabling technology
There are several widely available consumer-grade apps that allow the user to spoof a phone number, display a fake name, and send a message directly to voicemail or text. In the name of privacy, they offer anonymity to the sender, making it extremely hard to trace. Though the phone companies are working to identify and warn users that such messages may be fake, more customizable and concealable apps are available for sale on the dark web.
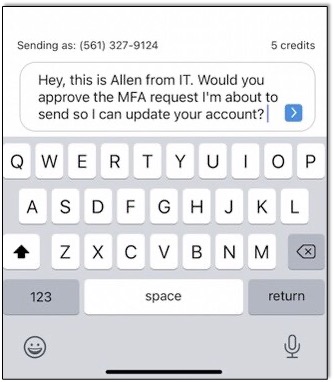
As with email, these provide scammers with the ability to deliver malicious phishing links to a broad audience. One click could download malware to your device or take you to a website that will attempt to harvest your credentials. But more troubling is the advanced spear-phishing abilities they provide. We might suspect a direct request for money (or gift certificates) or something obvious. However, consider the image above and ask yourself how many of your employees would immediately comply just to be helpful. If they do, it could render your multi-factor authentication meaningless.
Protecting yourself and your company
There are several other ways smishing can put your organization at risk, and there’s only so much technology can do to protect. With that in mind, here are several things you can do to make sure you and your organization don’t become smishing victims.
- Remember that a legitimate person or company sending you a text message will want you to be wary and check.
- Even if you recognize the company, think about other texts you’ve received from them. Most pay services, like Venmo and PayPal for example, include “we will never call or email you to request this PIN.” Most banks tell you to login to their site rather than include a URL in the text.
- Even if the phone number looks correct, remember that numbers and names are easily spoofed. A strong phish may email, text, and call you so that you feel like someone has backed up the claim that it’s legit.
- A true alert should provide a way for you to take the requested action without using the text. Login to a trusted URL that you have bookmarked. Call the number on the back of your credit card to confirm. Or, reach out in some other way that doesn’t rely on information provided by the same person or company.
- Messaging apps often provide a way that you can report spam, scams, and phishes. Reporting them helps them block further attacks and makes it harder and more expensive for the hacker to continue.
The bottom line is that any form of electronic communication is subject to compromise by a determined hacker and there is an ongoing “arms race” between hackers and the experts working to keep us safe. That’s why personal vigilance will always be the most important security measure in our cybersecurity toolkit.