Financial and Banking Pentesting
Penetration testing tailored for the financial services sector
Protecting financial systems can be complex
Unfortunately it’s not just the banks that are being targeted. Recent data breach numbers indicate hackers are targeting the entire financial sector. It’s one of our favorite sectors because we can easily demonstrate value and make a strong impact. We’re here to help make sure the hackers move to an easier target than you.
Raxis works closely with banks, investment firms, and credit unions to validate the proper operation of security controls protecting the systems used to manage financial operations.
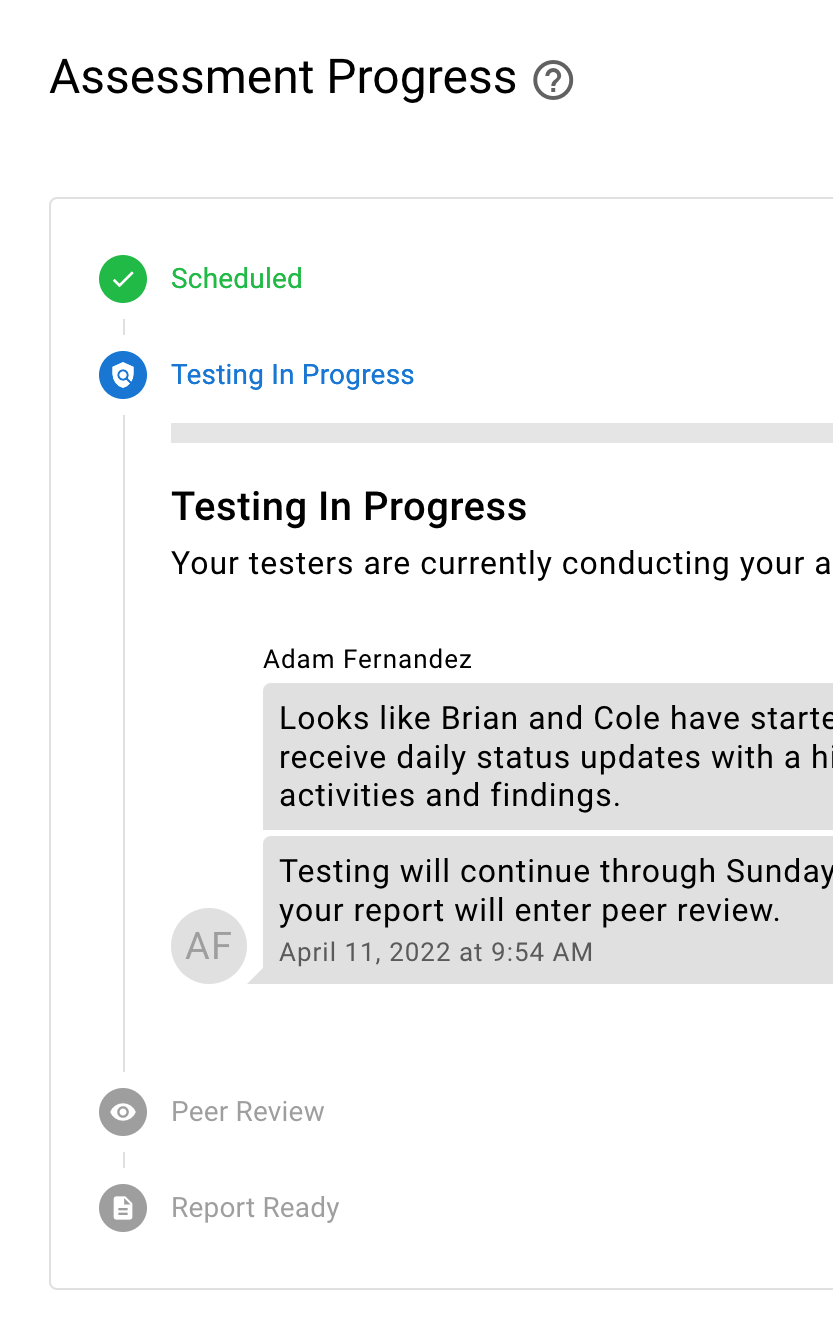
PTaaS provides non-stop monitoring
Raxis PTaaS provides a non-stop view of your network by performing financial penetration testing on demand and monitoring your network for changes. Financial institutions need this constant watch to ensure that emerging threats are kept at bay. Communicate in real time with your penetration testers, check on results as they arrive, and download your report securely.
Even with the most advanced vulnerability management tools, gaps in protection can occur due to a misconfiguration or missed patches. In some cases, rogue devices appear that can externally expose the banking network.
Hackers are not always after transferring money
Data breaches continue to rise year after year. While it may seem as though hackers are only interested in stealing money, they are more often after Personally Identifiable Information (PII), as it can be used to create illegal bank accounts under the victim’s identity.
The pace of new banking cybersecurity recommendations has accelerated over the past years in an attempt to thwart the ever-increasing threats. From best practices to annual testing requirements, there are a lot of very specific security procedures that need to be followed in order to remain compliant and hopefully safe from outside attacks.
In addition, PII data is often sold on the dark web, or black market, to monetize the results from a hack. Once this data reaches the hands of thieves, the costs are substantial in both dollar value and reputation damage. Raxis specializes in real penetration testing, which includes a live-fire attempt at safely copying critical data to demonstrate the risk.

