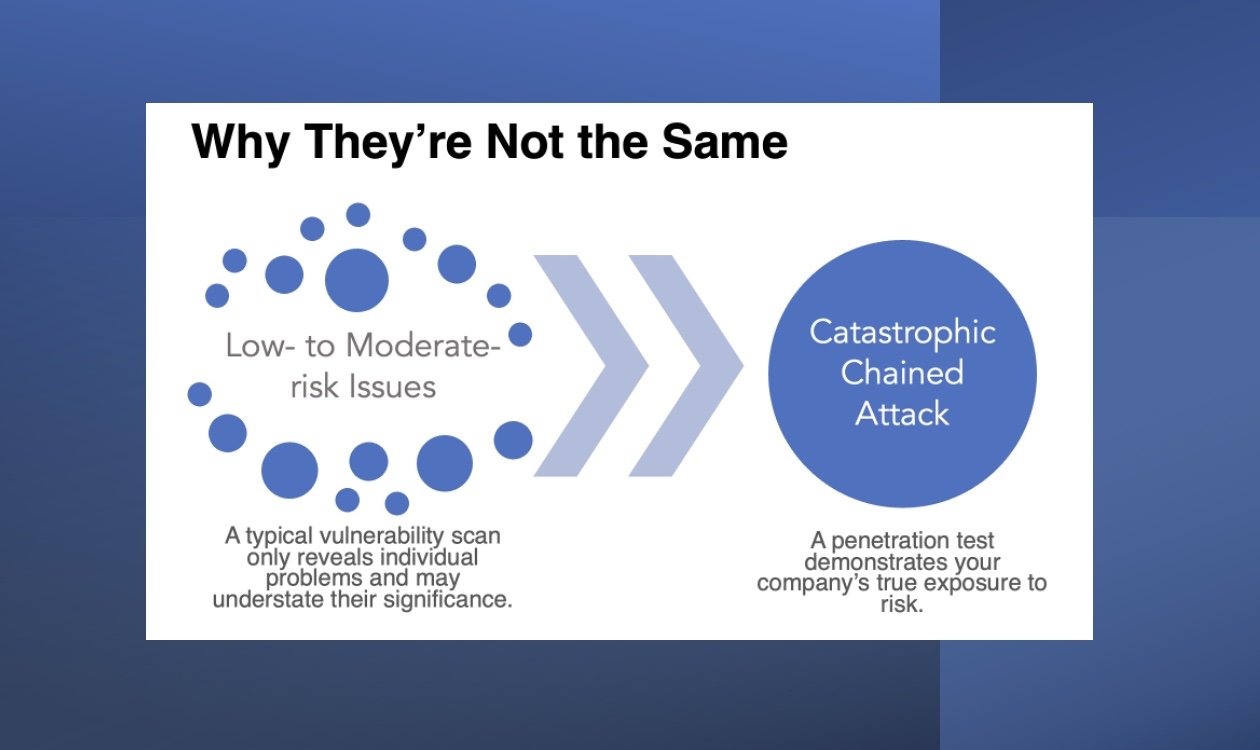
Chained Attacks and How a Scan Can Leave You Vulnerable
Vulnerability scans are useful tools for protecting your network. Find out why you shouldn’t rely[…]

2870 Peachtree Road
Suite #915-8924
Atlanta, GA 30305 USA
+1 678.421.4544
© 2024 Raxis, LLC – All rights reserved
