Wireless Series: The Aircrack-ng Suite for All Your Wireless Pentesting Needs
Principal Penetration Tester Scottie Cole continues our wireless series with the Aircrack-ng Suite, a set of tools for wireless pentest discovery and exploits.
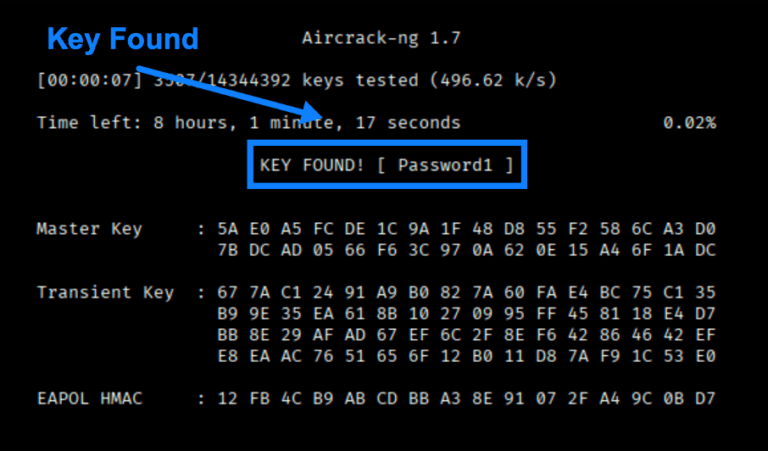
Principal Penetration Tester Scottie Cole continues our wireless series with the Aircrack-ng Suite, a set of tools for wireless pentest discovery and exploits.

Reynolds poses a new type of threat by including a Bring Your Own Vulnerable Driver (BYOVD) in the ransomware bundle, making it harder for EDR tools to catch.

While BeyondTrust patched cloud-hosted Remote Support customers earlier this month, on-premises deployments of BeyondTrust must manually patch to remediate.
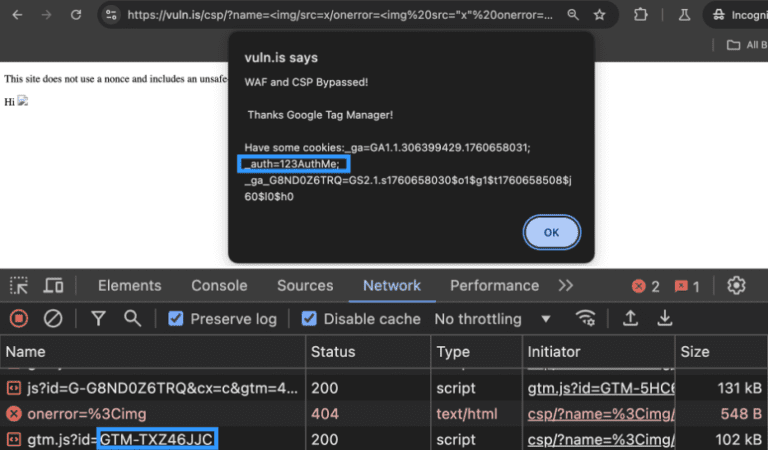
Ryan Chaplin takes an in-depth look at how attackers can use unsafe directives to bypass CSP, notably in Google Tag Manager, and how to remediate the issue.

With exploit code available for the vulnerabilities in Eaton’s xComfort Ethernet Communication Interface, Jason Taylor recommends replacing or isolating.