Wireless Series: Using Wifite to Capture and Crack a WPA2 Pre-Shared Key for Penetration Testing
Principal Penetration Tester Scottie Cole begins our wireless penetration testing series with capturing and cracking a WPA2 Pre-Shared Key using Wifite.
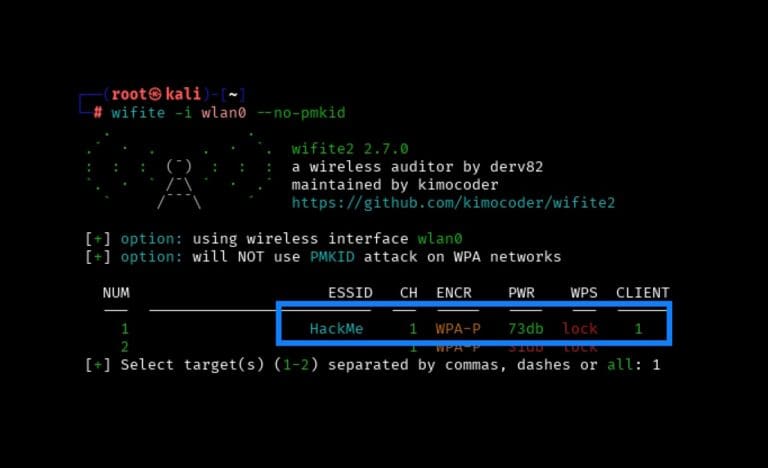
Principal Penetration Tester Scottie Cole begins our wireless penetration testing series with capturing and cracking a WPA2 Pre-Shared Key using Wifite.

Lead Penetration Tester Jason Taylor takes us step-by-step through jailbreaking an iPad 7 for use in penetration testing.

Raxis lead penetration tester, Nathan Anderson, continues our PSE & Red Team series with a discussion on the tools and techniques to bypass entry controls.
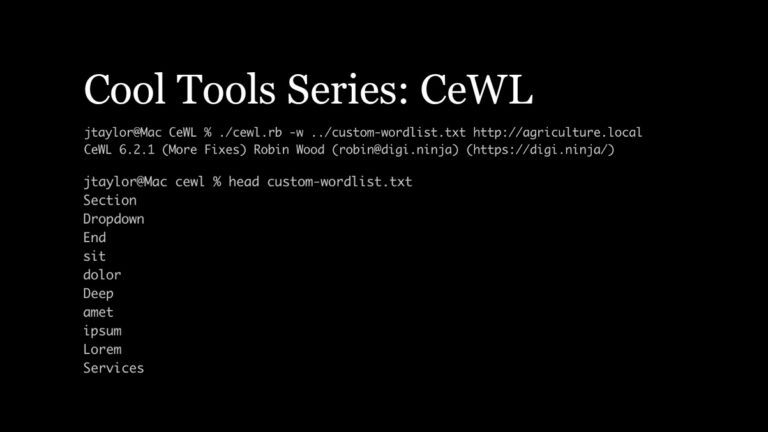
Lead Penetration Tester Jason Taylor discusses how the CeWL Custom Word List generator can improve hashcat results for penetration testing.
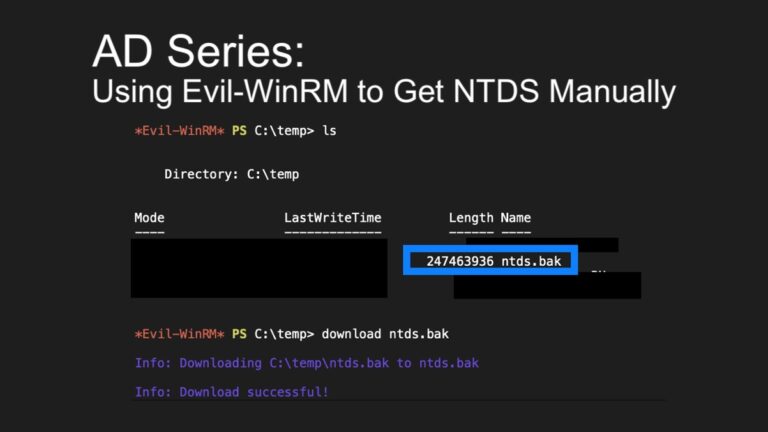
Principal Penetration Tester Andrew Trexler’s Active Directory series is back, showing how to use Evil-WinRM to copy NTDS.dit manually in penetration tests.