Data Theft Exploit Part 2: DNS Exfiltration Attack
Raxis’ Jason Taylor is back with a detailed tutorial on performing both manual and automated DNS exfiltration attacks for pentesting.

Raxis’ Jason Taylor is back with a detailed tutorial on performing both manual and automated DNS exfiltration attacks for pentesting.

With the start of 2026, the Raxis team is already busy. A new upgrade to our password-cracking system shows how quickly 8-character passwords can be cracked.

Raxis Lead Penetration Tester Jason Taylor’s in-depth tutorial explains setting up a server for DNS exfiltration. Check back next month to run the attack.

Microsoft Windows recently announced the removal of local-only installs on Windows 11. Raxis’ Ryan Chaplin looks at concerns and possible options.
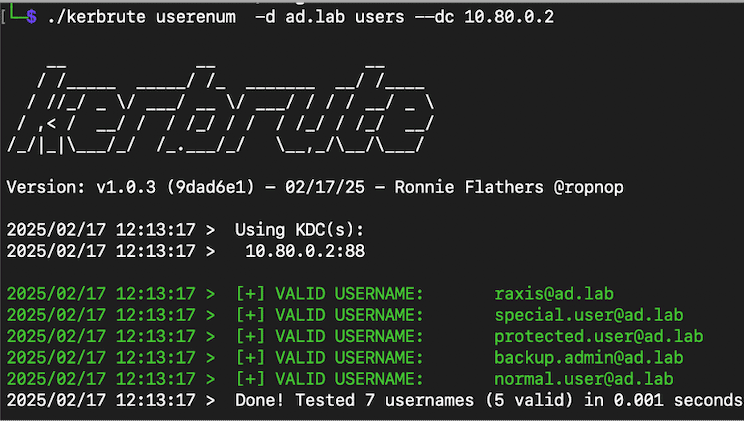
Raxis Principal Penetration Tester Andrew Trexler walks through the many uses of Kerbrute from user enumeration to brute-forcing and password spraying.