Choosing a Penetration Testing Company: Part 3
Caroline Kelly concludes our three-part “Choosing a Penetration Testing Company” series with how Penetration Testing as a Service (PTaaS) provides great value.

Caroline Kelly concludes our three-part “Choosing a Penetration Testing Company” series with how Penetration Testing as a Service (PTaaS) provides great value.
Lead Penetration Tester Jason Taylor looks at OWASP’s Top 10 list for LLM applications for penetration testing as AI machine learning becomes prevalent.

Brad Herring continues our three-part “Choosing a Penetration Testing Company” series with a look at the factors to consider when choosing the best vendor.
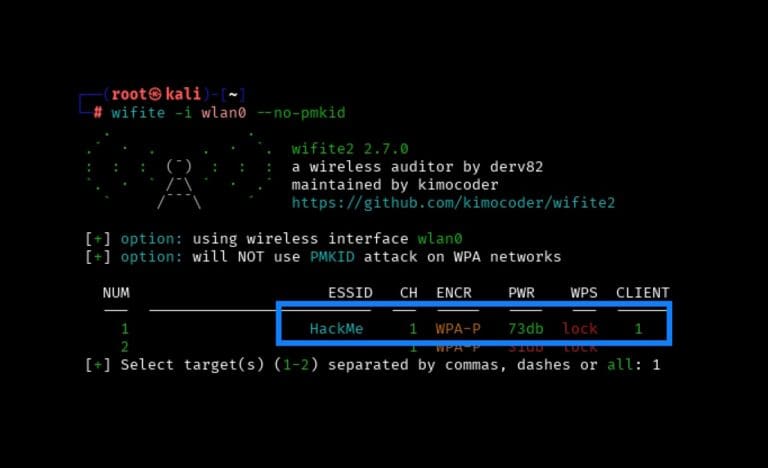
Principal Penetration Tester Scottie Cole begins our wireless penetration testing series with capturing and cracking a WPA2 Pre-Shared Key using Wifite.

Cole Stafford starts our three-part “Choosing a Penetration Testing Company” series by looking at what penetration testing is and the types of penetration tests.